Space Pirates
FLAG_LEN = 30
TARGET = [
0x5A,0x3D,0x5B,0x9C,0x98,0x73,0xAE,0x32,0x25,0x47,
0x48,0x51,0x6C,0x71,0x3A,0x62,0xB8,0x7B,0x63,0x57,
0x25,0x89,0x58,0xBF,0x78,0x34,0x98,0x71,0x68,0x59
]
XOR_KEY = [0x42, 0x73, 0x21, 0x69, 0x37]
MAGIC_ADD = 0x2A # 0x2A = 42
def decrypt_pirate_flag():
buffer = TARGET.copy()
for i in range(FLAG_LEN):
buffer[i] ^= i
for i in range(FLAG_LEN):
buffer[i] = (buffer[i] - MAGIC_ADD) % 256
for i in range(0, FLAG_LEN, 2):
buffer[i], buffer[i+1] = buffer[i+1], buffer[i]
for i in range(FLAG_LEN):
buffer[i] ^= XOR_KEY[i % 5]
flag = bytes(buffer).decode('ascii')
return flag
if __name__ == "__main__":
flag = decrypt_pirate_flag()
print(f"Flag: {flag}")Are You Pylingual?
先使用解包pyc的工具去解包,得到
import pyfiglet
file = open('flag.txt', 'r')
flag = file.read()
font = 'slant'
words = 'MASONCC IS THE BEST CLUB EVER'
flag_track = 0
art = list(pyfiglet.figlet_format(words, font=font))
i = len(art) % 10
for ind in range(len(art)):
if ind == i and flag_track < len(flag):
art[ind] = flag[flag_track]
i += 28
flag_track += 1
art_str = ''.join(art)
first_val = 5
second_val = 6
first_half = art_str[:len(art_str) // 2]
second_half = art_str[len(art_str) // 2:]
first = [~ord(char) ^ first_val for char in first_half]
second = [~ord(char) ^ second_val for char in second_half]
output = second + first
print(output)然后写一个解密脚本
import pyfiglet
output = [-90, -42, -39, -42, -39, -39, -39, -42, -39, -42, -39, -42, -39, -42, -39, -90, -90, -39, -48, -13, -52, -39, -42, -39, -42, -39, -42, -39, -42, -90, -42, -39, -42, -39, -90, -90, -42, -39, -39, -39, -39, -42, -39, -90, -90, -39, -39, -42, -105, -90, -90, -42, -39, -39, -91, -90, -90, -39, -91, -39, -42, -39, -42, -39, -39, -39, -39, -42, -39, -42, -39, -39, -39, -42, -39, -42, -34, -39, -39, -42, -39, -42, -39, -42, -39, -42, -39, -90, -90, -39, -39, -123, -13, -39, -42, -39, -42, -39, -42, -39, -90, -90, -39, -39, -115, -39, -42, -90, -90, -90, -39, -39, -39, -42, -39, -42, -90, -42, -39, -42, -39, -42, -90, -90, -90, -39, -90, -90, -90, -42, -39, -42, -90, -39, -42, -39, -39, -39, -39, -42, -39, -42, -90, -90, -90, -42, -39, -42, -90, -90, -90, -42, -39, -42, -90, -42, -39, -42, -39, -42, -68, -42, -39, -42, -39, -13, -42, -90, -42, -39, -42, -90, -42, -39, -42, -90, -42, -90, -90, -90, -90, -90, -42, -39, -39, -42, -90, -90, -105, -90, -90, -42, -90, -90, -90, -90, -90, -42, -42, -90, -90, -90, -90, -42, -42, -90, -42, -39, -39, -39, -39, -39, -91, -90, -90, -90, -102, -42, -90, -90, -90, -90, -90, -42, -91, -90, -90, -90, -90, -42, -90, -90, -90, -90, -90, -42, -39, -39, -13, -39, -39, -39, -39, -39, -85, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -128, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -119, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -13, -39, -39, -39, -39, -90, -90, -90, -90, -90, -90, -90, -39, -39, -39, -39, -90, -115, -90, -90, -90, -90, -90, -90, -90, -90, -90, -90, -39, -13, -39, -39, -39, -42, -39, -90, -90, -90, -90, -42, -39, -123, -39, -39, -42, -56, -42, -39, -90, -90, -90, -90, -42, -39, -90, -90, -39, -91, -13, -39, -39, -42, -39, -90, -90, -42, -39, -39, -123, -39, -123, -39, -42, -106, -42, -39, -90, -90, -42, -39, -42, -39, -42, -90, -42, -39, -42, -13, -39, -42, -39, -42, -90, -90, -90, -39, -39, -123, -39, -123, -42, -73, -42, -39, -42, -90, -90, -90, -42, -39, -90, -43, -39, -90, -42, -39, -13, -42, -90, -90, -90, -90, -90, -42, -39, -39, -123, -90, -90, -124, -42, -90, -90, -90, -90, -90, -42, -90, -42, -39, -123, -90, -123, -39, -39, -13, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -39, -13, -38, -38, -118, -38, -91, -91, -38, -38, -91, -91, -91, -91, -91, -91, -38, -38, -38, -91, -91, -91, -91, -91, -38, -91, -91, -91, -91, -38, -38, -91, -103, -38, -38, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -38, -38, -38, -91, -91, -91, -91, -91, -91, -91, -91, -114, -16, -38, -38, -38, -43, -38, -38, -122, -43, -38, -38, -43, -38, -38, -38, -122, -38, -43, -38, -91, -91, -91, -43, -43, -38, -91, -91, -100, -90, -43, -38, -122, -38, -43, -38, -43, -38, -91, -91, -91, -91, -43, -38, -91, -91, -91, -91, -43, -38, -38, -43, -38, -38, -91, -43, -127, -91, -91, -91, -43, -16, -38, -38, -43, -38, -43, -122, -91, -43, -38, -43, -38, -43, -122, -38, -122, -38, -90, -91, -91, -38, -90, -43, -107, -43, -38, -43, -38, -43, -38, -38, -122, -43, -38, -43, -38, -43, -38, -38, -38, -43, -38, -43, -38, -38, -38, -38, -38, -38, -38, -43, -104, -43, -38, -90, -91, -91, -38, -90, -38, -16, -38, -43, -38, -43, -38, -38, -43, -38, -43, -38, -91, -91, -91, -38, -122, -91, -91, -91, -68, -38, -43, -38, -43, -91, -43, -38, -43, -38, -43, -122, -38, -38, -43, -38, -43, -91, -91, -91, -43, -38, -43, -91, -91, -91, -38, -38, -113, -91, -43, -38, -43, -38, -91, -91, -91, -43, -38, -43, -38, -16, -43, -91, -43, -38, -38, -43, -91, -43, -91, -43, -38, -38, -122, -91, -119, -91, -91, -91, -91, -43, -90, -91, -91, -91, -91, -43, -91, -43, -38, -122, -91, -43, -90, -91, -91, -91, -91, -43, -90, -91, -91, -91, -103, -43, -38, -38, -43, -91, -91, -91, -43, -43, -91, -91, -91, -91, -43, -38, -38, -16, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -50, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -114, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -38, -16, -38, -38, -91, -91, -91, -91, -109, -91, -91, -91, -38, -38, -91, -91, -91, -91, -91, -91, -91, -91, -38, -38, -38, -91, -91, -91, -91, -38, -38, -91, -91, -91, -91, -91, -54, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -91, -38, -38, -38, -91, -91, -91, -91, -91, -91, -91, -91, -38, -38, -38, -38, -91, -108, -38, -38, -91, -91, -91, -91, -91, -91, -38, -16, -38, -43, -91, -38, -38, -91, -91, -43, -38, -43, -38, -43, -38, -43, -38, -91, -91, -91, -91, -43, -38, -38, -43, -38, -91, -91, -38, -45, -43, -38, -91, -91, -91, -91, -43, -38, -91, -91, -91, -43, -91, -38, -38, -91, -91, -109, -38, -38, -43, -38, -91, -91, -91]
L = len(output)
second_len = L - L // 2
first_len = L // 2
second_enc = output[:second_len]
first_enc = output[second_len:]
first_half_chars = []
for y in first_enc:
x = ~(y ^ 5)
x = x & 0xFF
first_half_chars.append(chr(x))
second_half_chars = []
for y in second_enc:
x = ~(y ^ 6)
x = x & 0xFF
second_half_chars.append(chr(x))
art_str = ''.join(first_half_chars) + ''.join(second_half_chars)
words = 'MASONCC IS THE BEST CLUB EVER'
font = 'slant'
original_art = pyfiglet.figlet_format(words, font=font)
n_original = len(original_art)
i = n_original % 10
flag_chars = []
pos = i
while pos < n_original:
flag_chars.append(art_str[pos])
pos += 28
flag = ''.join(flag_chars)
print("flag:", flag)
#flag: pctf{obFusc4ti0n_i5n't_EncRypt1oN}Space Pirates 2
TARGET = [
0x15, 0x5A, 0xAC, 0xF6, 0x36, 0x22, 0x3B, 0x52, 0x6C, 0x4F,
0x90, 0xD9, 0x35, 0x63, 0xF8, 0x0E, 0x02, 0x33, 0xB0, 0xF1,
0xB7, 0x69, 0x42, 0x67, 0x25, 0xEA, 0x96, 0x63, 0x1B, 0xA7,
0x03, 0x0B
]
XOR_KEY = [0x7E, 0x33, 0x91, 0x4C, 0xA5]
ROTATION_PATTERN = [1, 3, 5, 7, 2, 4, 6]
MAGIC_SUB = 0x5D
def rotate_right(byte: int, n: int) -> int:
n = n % 8
if n == 0:
return byte
return ((byte >> n) | (byte << (8 - n))) & 0xFF
def inverse_coordinate_calibration(buffer: bytearray):
for i in range(len(buffer)):
pos_sq = (i * i) % 256
buffer[i] ^= pos_sq
def inverse_temporal_inversion(buffer: bytearray):
CHUNK_SIZE = 5
for chunk_start in range(0, len(buffer), CHUNK_SIZE):
chunk_end = min(chunk_start + CHUNK_SIZE, len(buffer))
buffer[chunk_start:chunk_end] = buffer[chunk_start:chunk_end][::-1]
def inverse_gravitational_shift(buffer: bytearray):
for i in range(len(buffer)):
buffer[i] = (buffer[i] + MAGIC_SUB) % 256
def inverse_spatial_transposition(buffer: bytearray):
for i in range(0, len(buffer), 2):
if i + 1 < len(buffer):
buffer[i], buffer[i+1] = buffer[i+1], buffer[i]
def inverse_stellar_rotation(buffer: bytearray):
for i in range(len(buffer)):
rotation = ROTATION_PATTERN[i % 7]
buffer[i] = rotate_right(buffer[i], rotation)
def inverse_quantum_cipher(buffer: bytearray):
for i in range(len(buffer)):
buffer[i] ^= XOR_KEY[i % 5]
if __name__ == "__main__":
buffer = bytearray(TARGET)
inverse_coordinate_calibration(buffer)
inverse_temporal_inversion(buffer)
inverse_gravitational_shift(buffer)
inverse_spatial_transposition(buffer)
inverse_stellar_rotation(buffer)
inverse_quantum_cipher(buffer)
flag = buffer.decode('utf-8')
print(f"Flag: {flag}")
#Flag: PCTF{Y0U_F0UND_TH3_P1R4T3_B00TY}Space Pirates 3
def rotate_right(b, n):
n = n % 8
return ((b >> n) | (b << (8 - n))) & 0xFF
target = [
0x60, 0x6D, 0x5D, 0x97, 0x2C, 0x04, 0xAF, 0x7C, 0xE2, 0x9E,
0x77, 0x85, 0xD1, 0x0F, 0x1D, 0x17, 0xD4, 0x30, 0xB7, 0x48,
0xDC, 0x48, 0x36, 0xC1, 0xCA, 0x28, 0xE1, 0x37, 0x58, 0x0F
]
xor_key = [0xC7, 0x2E, 0x89, 0x51, 0xB4, 0x6D, 0x1F]
rotation_pattern = [7, 5, 3, 1, 6, 4, 2, 0]
magic_sub = 0x93
chunk_size = 6
def decrypt_vault(ciphertext):
buffer = bytearray(ciphertext)
print("[6] Reversing coordinate calibration...")
for i in range(len(buffer)):
pos_val = (i * i + i) % 256
buffer[i] ^= pos_val
print("[5] Reversing temporal inversion...")
for chunk_start in range(0, len(buffer), chunk_size):
chunk_end = min(chunk_start + chunk_size, len(buffer))
chunk = buffer[chunk_start:chunk_end]
buffer[chunk_start:chunk_end] = chunk[::-1]
print("[4] Reversing gravitational shift...")
for i in range(len(buffer)):
buffer[i] = (buffer[i] + magic_sub) % 256
print("[3] Reversing spatial transposition...")
for i in range(0, len(buffer) - 1, 2):
buffer[i], buffer[i+1] = buffer[i+1], buffer[i]
print("[2] Reversing stellar rotation...")
for i in range(len(buffer)):
rotation = rotation_pattern[i % len(rotation_pattern)]
buffer[i] = rotate_right(buffer[i], rotation)
print("[1] Reversing quantum cipher...")
for i in range(len(buffer)):
buffer[i] ^= xor_key[i % len(xor_key)]
return buffer.decode('ascii')
if __name__ == "__main__":
flag = decrypt_vault(target)
print(f"\nFlag: {flag}\n")
#Flag: PCTF{M4ST3R_0F_TH3_S3V3N_S34S}ReadMyNote
运行程序,发现有验证年份。于是搜索2025的字符串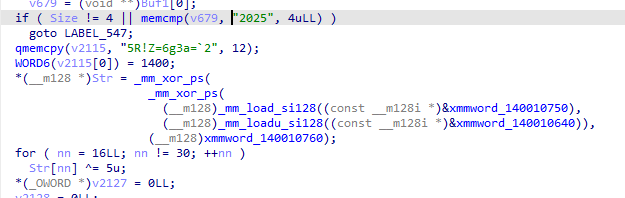 给2025下断,然后单步执行找可能的加密函数
给2025下断,然后单步执行找可能的加密函数
然后发现str就是解密过后的flag
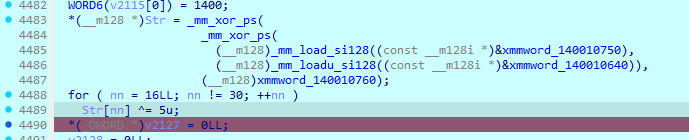
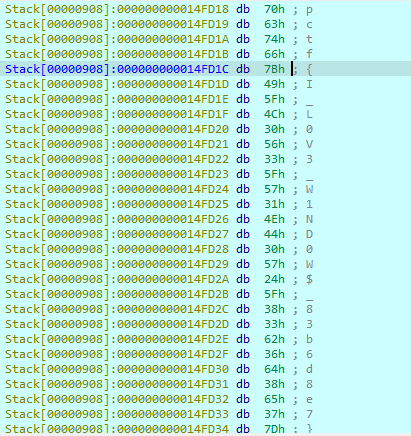
Vorpal Masters
打开IDA看一下
def find_valid_license_key():
v6_fixed = "CACI"
s1_fixed = "PatriotCTF"
v4_solutions = []
for v4 in range(-5000, 10001):
left = (v4 + 22) % 1738
right = 6 * ((2 * v4) % 2000) + 9
if left == right:
v4_solutions.append(v4)
if v4_solutions:
for v4 in v4_solutions:
print(f"{v6_fixed}-{v4}-{s1_fixed}")
if __name__ == "__main__":
find_valid_license_key()