chaos
打开程序即可获取flag
chaos2
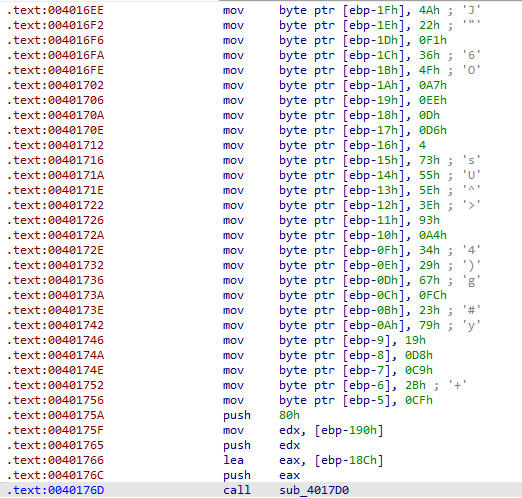
一长串mov,明显是加密数据之类的,然后紧接着跳转sub_4017D0,明显其是校验函数之类的.
.text:0040175A push 80h ; ; 128字节
.text:0040175F mov edx, [ebp-190h]
.text:00401765 push edx ; 密钥位置
.text:00401766 lea eax, [ebp-18Ch]
.text:0040176C push eax ; S盒
.text:0040176D call sub_4017D0 ; RC4初始化100H,256其实也能想到是RC4加密。
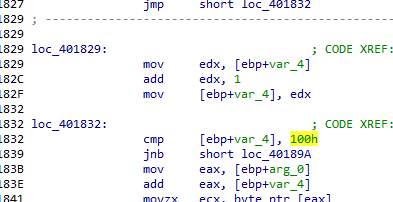 不过需要注意的是
不过需要注意的是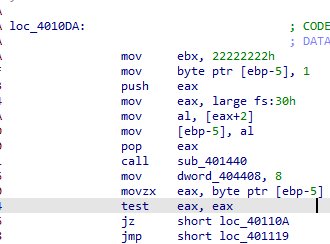 如果没有检测到调试之类的就会对密钥特定偏移进行修改
如果没有检测到调试之类的就会对密钥特定偏移进行修改
def rc4_init(key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def rc4_crypt(S, data):
i = 0
j = 0
out = []
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = S[(S[i] + S[j]) % 256]
out.append(byte ^ k)
return bytes(out)
enc_data = [
0x0F, 0x1A, 0x8A, 0x5A, 0x22, 0xAB, 0x1E, 0x63, 0x19, 0x5A, 0x87, 0xF2, 0xE6, 0xE9, 0xD7, 0xD1,
0x97, 0xF9, 0xF8, 0x32, 0x5B, 0xDE, 0x2D, 0xD6, 0xA3, 0x4F, 0x7E, 0xCB, 0x61, 0xB2, 0x3F, 0xBF,
0xB7, 0x1B, 0x0A, 0x84, 0xB3, 0xB4, 0xDE, 0x03, 0x46, 0x7B, 0x83, 0xF0, 0xC4, 0xB3, 0xAB, 0x7B,
0x29, 0xBC, 0x1F, 0xFE, 0x8A, 0x79, 0x26, 0xDA, 0x08, 0x01, 0x85, 0x66, 0x7D, 0xBB, 0xEE, 0x0F,
0x89, 0x59, 0xD4, 0x5F, 0xAC, 0x18, 0xAE, 0x0B, 0x4E, 0xF0, 0xB7, 0x05, 0x5C, 0x81, 0x04, 0x9F,
0xA4, 0x1C, 0x5D, 0xA0, 0xB9, 0x07, 0x92, 0x5C, 0x8A, 0x53, 0xF3, 0xFF, 0xF7, 0xA7, 0xDD, 0x2E,
0xE6, 0xED, 0x0F, 0x77, 0x2C, 0x4A, 0x22, 0xF1, 0x36, 0x4F, 0xA7, 0xEE, 0x0D, 0xD6, 0x04, 0x73,
0x55, 0x5E, 0x3E, 0x93, 0xA4, 0x34, 0x29, 0x67, 0xFC, 0x23, 0x79, 0x19, 0xD8, 0xC9, 0x2B, 0xCF
]
key_bytes = b'flag:{Th1sflaglsG00ds}' + b'\x00' * 106
key = list(key_bytes)
key[8] = ord('i')
key[14] = ord('I')
key[17] = ord('o')
key[18] = ord('o')
S = rc4_init(key)
dec_data = rc4_crypt(S, enc_data)
flag = dec_data.decode('ascii')
print(f"解密后的flag: {flag}")